I recently discovered a very useful tool: SSH tunnels. Not only are they practical for browsing privately and securely, but they can also allow us to reach servers or services which we do not have access from the computer we are connecting to.
First I will explain how it works and later the implementation that I have done in my particular case.
How does it work?
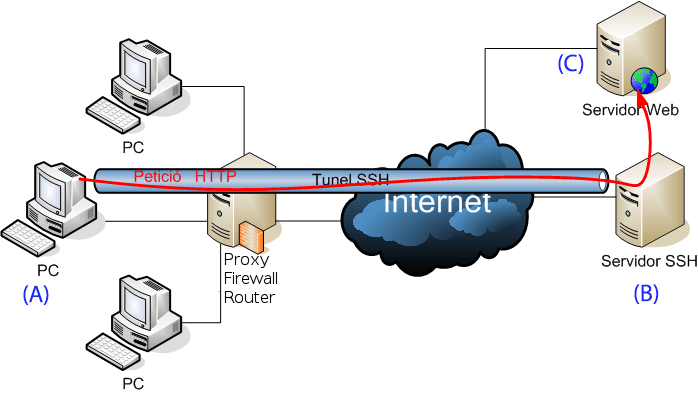
We could summarize it saying, that an SSH tunnel allows us to communicate from computer A to computer C (for example a web server) as if we were connecting from computer B (intermediate server). Another way of saying it would be by explaining that B impersonates A from the point of view of C.
Surely the best way to see it is through images. The usual way to connect to a website follows a scheme like this:
But this type of connection presents security problems if we are connecting from a public network (airport, coffee shop, library …) where our communications can be spied on, even before reaching the Internet, by users connected to the same network as us.
One way to avoid this is that the computer that is in charge of communicating with the web is outside the public network so that our data is less in dangerous, but obviously, we will need secure the communication between our computer (A) and the intermediate server (B). One way to do this is to initiate communication between these two computers by SSH, which is an encrypted protocol.
The proposed communication scheme would be similar to this (obviously the SSH server will not have a direct connection to the web server, but will go through the Internet, but I hope it’s understood).
In this way our computer will have a secure connection to the web (C) and it is also possible that we can skip some security measure configured in the firewall / proxy of the public network in which we are connected, since having an encrypted connection between our computer and the intermediate server, they can’t know that it’s communicating through the “tunnel” and obviously they can’t act over the communication that the SHH server (B) has with the web server, since it’s outside from their network.
As I said before, this architecture can also be very useful in the event that we have to remotely access a server which we don’t have permissions from the computer we are. For example, we are on “vacation” and we have to re-start a company database server that can only be accessed from within the business network. Although the best system to do this would be connecting to the corporate VPN, the proposed system would be an alternative if the company has a server with Internet access to which we could open an SSH tunnel, in order to connect to the database server. as if you were doing it from inside the business network.
Implementation
The theory is explained in the previous section so that you understand the concept and be able to implement it in a way that is useful in your case.
Anyway, as an example, I will explain how I have implemented it working with Windows clients.
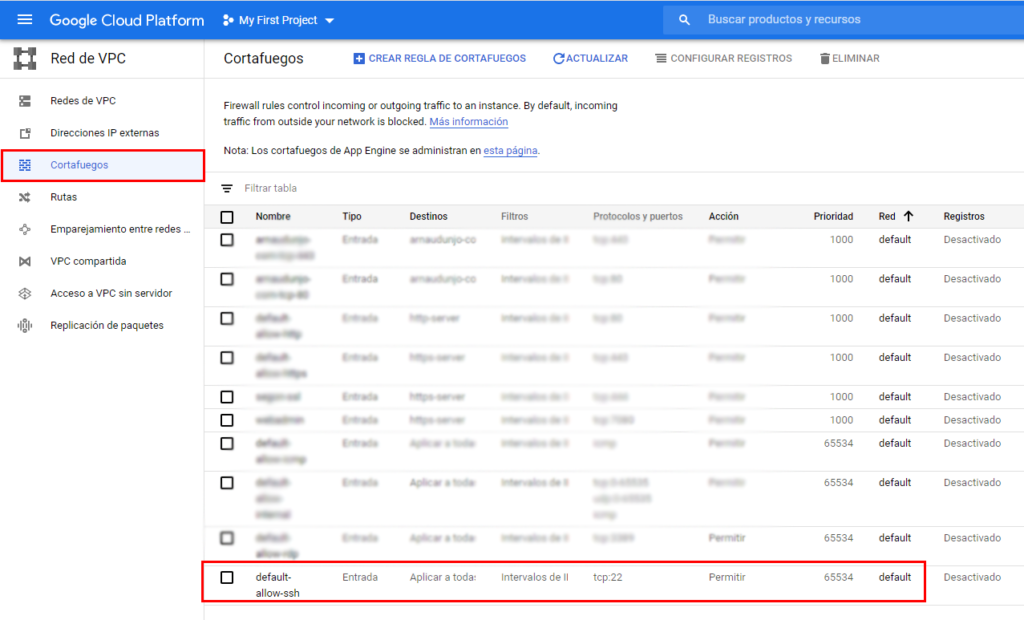
As I mentioned before, an computer outside from public network it’s necessary to act as a bridge between the computer you are and the one you want to reach (typically a web server). This process has practically no effect over performance on any current computer, I use the Google Cloud instance. To do this, you just have to make sure that the port it will use is open (by default 22) and you have started the SSH service to connect to the server (in my case, I use the client PuTTy)
You will have to have a specific configuration both in the Putty and in the programs that you want to use the SSH connection.
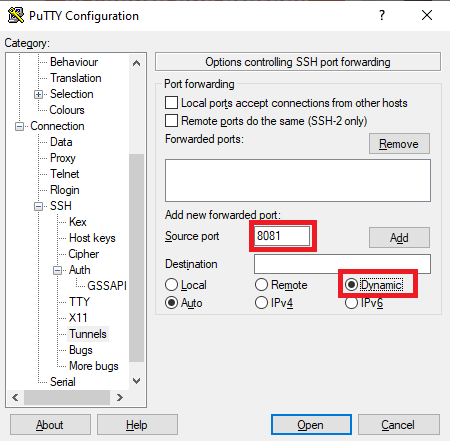
Your SSH client must configure it so that you redirect the ports of your computer to those of the server. This in the case of the Putty you can do it like this (Connection-> SHH-> Tunnels)
In this case, it is not particularly interesting to know against which server port the client computer port is mapped, but as you can see it could be configured.
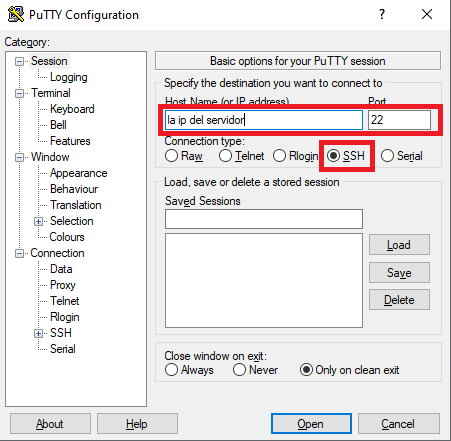
Then you can connect normally to the server by SSH
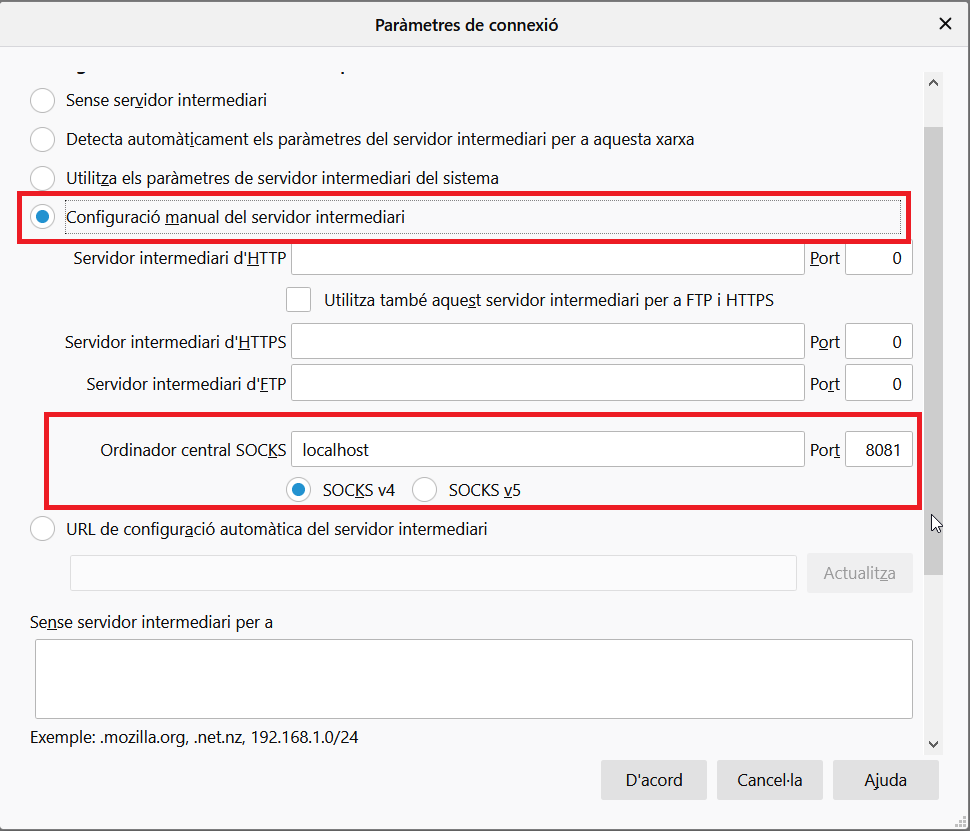
We still have to configure the program that you want to use privately so that it is thought that we are behind a proxy and that it must use a specific port (the same port that we have configured in the SSH client). In the case of Firefox (Options-> General-> Network settings)
From now on, as long as we have logged in to the server via PuTTy, communications between our device and the rest of the Internet will be passed through the server we have configured, and how the communication between the two is encrypted, we can say it’s safe.
Limitations
The only disadvantage that this system has is that the firewall of the network where we are connected must allow the connection to the port that we use to establish the connection (in the case of the example, port 22). It is not usual for public networks, so ideally, instead of opening port 22 on the server, try to use one that rarely closed by a public network, such as port 80 (http) or 443 (https).
It is probable that our server has these ports used for another service (a web server for example). In another post I will explain how to use the same port for different services so that we can skip this limitation.
Source : https://geekland.eu/que-es-y-para-que-sirve-un-tunel-ssh/